What Is Business Profile Hijacking & How You Can Protect Your Business

What is Business Profile Hijacking?
Search engines automatically create a business listing based on publicly available information, but they permit business owners to override this automatic listing by publishing their own. This listing may include business hours, slogan, geographical location, a website link, contact information, reviews, and images. Business owners are also permitted to respond to reviews.
Recently, Sedara has seen incidents in which the attacker claims control over a business listing that they do not own. Once they’ve claimed the business, they edit the phone number and website listing, or they add disparaging images, slogans, or responses to reviews.
There are several possible motivations for falsely claiming a business. A competitor could send traffic to their own website or phone number. The attacker could also be an activist or prankster, or cybercriminals could redirect users to a malicious website to collect private information.
Search engines have taken action to prevent attackers from falsely claiming businesses – for example, requiring verification from a company-owned email address. However, attackers can subvert this verification process by claiming an email address from the target organization, answering an unmonitored phone on-site, or convincing a targeted employee to approve the verification email. After a business profile has been “verified” and claimed by an attacker, they can use their own account to modify the information. It can be a difficult process to transfer ownership back to the correct party.
This attack is not unique to Google. It’s possible with Bing, Yelp, Facebook, and other search engines or business directories.
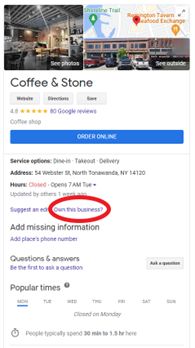
To check your business profile, search for your own organization’s name in a search engine. You can claim your business by clicking an “Own this business?” or “Claim this business” link, shown in an example below.
To prevent this attack, Sedara recommends organizations:
– Have the appropriate group claim the business listing on common search engines or business listings. Examples: Google, Bing, Facebook, Apple Maps, LinkedIn company directories, Instagram for Business.
– Periodically check business listings to ensure they are still accurate.
– Train employees to recognize phishing tactics, and instruct the owner of the business account that they are not to transfer ownership of the business profile to any unknown party.
Want help with securing your organization’s web presence?
Sedara can help review your organization’s web presence and exposure to the Internet, and provide recommendations to improve your security stance. If you want to learn more about proactive steps you can take to improve your security, check out our whiteboard series topic 5 tips for Improving Your Organization’s Security Awareness.