Network Detection and Response: Your FAQ’s Answered

What is Network Detection and Response (NDR), and why would I want it?
NDR provides another layer of visibility into what has or is currently happening on the network. Through this lens, you can detect threats that may be missed with perimeter and host-based tools such as firewalls, logs, and endpoint detection. You can also monitor devices that cannot be monitored through logs or have agents deployed on them, such as many IoT devices. NDR enables threat hunting through packet data, providing an authoritative source for validation.
How far along in my cybersecurity maturity do I need to be to add on NDR?
It depends, however, if you have compliance requirements that mandate monitoring network traffic for potential threats (some examples are PCI DSS, HIPAA, SOX, FISMA or CIP), and you already have a firewall, SIEM, and endpoint protection solutions in place, then NDR would likely be an excellent solution to add to your Extended Detection and Response (XDR) implementation.
How Does NDR fit into XDR?
First, let’s review what XDR is, Extended Detection and Response is a holistic approach to cybersecurity, integrating data from various security tools it helps security teams gain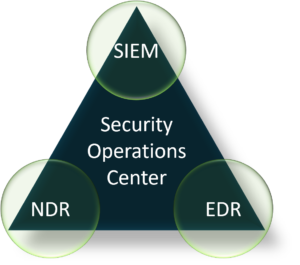 comprehensive visibility to respond to complex cyber threats effectively. This approach requires a way to monitor logs, endpoints, and network traffic. This trio is often referred to as the SOC visibility triad.
comprehensive visibility to respond to complex cyber threats effectively. This approach requires a way to monitor logs, endpoints, and network traffic. This trio is often referred to as the SOC visibility triad.
Adding NDR as a vector of visibility brings compounding value when used with the XDR approach alongside SIEM and EDR. As it brings in the context from assets in your internal network.
To break down the value of each source of data –
- SIEM – Collects logs; this is information on what a system reports happened.
- EDR – Tells you fine details about what is happening with an endpoint.
- NDR – Tells you what occurred around assets within your internal network, bringing an additional layer of valuable and confirmative context to any scenario.
How is NDR Deployed?
NDR is agent-less, and requires an appliance or software deployment. It can be either in-line or passive in deployment style. In-line acts like a “man-in-the-middle” and often requires real-time action to be taken as network traffic passes through the tool and can negatively impact network speed. Passive deployments are becoming more common and in this deployment style, NDR sits out of band, being connected to a network TAP or a SPAN port – mirroring all traffic to the NDR tool. This does not impact throughput and allows the device to remain silent to attackers.
How does an NDR solution collect data?
There are three primary ways in which an NDR solution collects Data.
- NetFlow Analysis: NDR solutions can analyze NetFlow data which provides information about the flow of network traffic, including the source and destination IP addresses, protocols used, and other metadata.
- Protocol Analysis: Where the behavior of specific network protocols, such as HTTP, FTP, or DNS is used to detect anomalies or malicious activity.
- Packet Capture: Capturing and analyzing every packet that passes through the network, allowing it to detect anomalies and threats in real-time.
Why would I use NDR when I can aggregate data with my firewall and send it to my SIEM?
NDR monitors for behavioral abnormalities inside the network, whereas a firewall typically built-in Intrusion Detection and Prevention Systems (IDPS) do not. By using a firewall instead of a true NDR, attackers only need to be right once to get what they want, and defenders need to be right all the time to protect data. Once the attacker is past the perimeter, there are uncovered blind spots where they can operate undetected. By adding NDR, the internal east-west traffic visibility is available for the SOC team monitoring your network, so when the attacker starts executing some type of discovery, this potentially abnormal activity is what gets flagged. Without the internal east-west traffic visibility, an attacker could operate within a network without any notification of issue.
What is the difference between NDR and IDS/IPS?
Intrusion Detection and Prevention Systems (IDS/IPS) and Network Detection and Response (NDR) are cybersecurity solutions that focus on combatting threats on the network. Take a look at the differences.
- Scope – NDR solutions provide visibility into the entire network, including on-premise and cloud environments. IDS/IPS solutions are typically deployed close to, or right at, the network perimeter to monitor and respond to inbound and outbound traffic.
- Detection Approach – NDR uses advanced analytics to identify patterns and anomalies that occur within the network. NDR also uses rule-based approaches for known-threat and signature-based detection. IDS/IPS only typically uses rule-based and signature-based detection approach. The anomalous behavior detection is why NDR supersedes traditional IDS/IPS for network threat detection.
- Response Capability – NDR solutions integrate into an XDR or security orchestration, automation and response (SOAR) platform to automate responses such as blocking suspicious traffic via a firewall integration or quarantining infected devices with an EDR integration. IDS/IPS solutions often have direct, but limited, response capabilities while deployed in-line.
- Deployment – NDR Solutions are typically deployed as standalone appliances or virtual machines while IDS/IPS solutions are often integrated into other security tools such as firewalls, however, sometimes IDS/IPS solutions are deployed standalone.
In summary, NDR complements the layered approach to cybersecurity and enhances overall cybersecurity maturity. By improving visibility and providing proactive defense against cyber threats, NDR empowers organizations to strengthen their incident response capabilities. By implementing NDR alongside existing security measures, businesses can significantly reduce the risk of data breaches and network disruptions, ensuring the confidentiality, integrity, and availability of their critical network resources.
How Can Sedara Help?
Sedara’s Security Operations Center can assist your organization in detecting and responding to threats through 24x7x365 monitoring. By utilizing Extended Detection and Response (XDR) and SIEM solutions, trained cybersecurity personnel are always monitoring your network.