NIST CSF 2.0 is Here. What Do You Need to Know?

NIST released the much-anticipated update to its popular Cybersecurity Framework (CSF) in February 2024. The NIST CSF is one of the most widely used cybersecurity frameworks, designed to help organizations of any size in any industry holistically start, mature, and sustain a cybersecurity program. The latest version of the NIST CSF—NIST CSF 2.0—brings several enhancements over the previous version. This article will cover what you need to know about the new NIST CSF 2.0.
What is the NIST CSF?
The NIST CSF is a cybersecurity framework that offers a roadmap for building a cybersecurity program that reduces risk. Some organizations, such as the federal government, are legally required to follow the NIST CSF; however, many other organizations voluntarily choose to follow it. The NIST CSF is made up of three components, including:
1. Framework Core
The Core is the most widely known and commonly used part of the NIST CSF. The Core describes the outcomes organizations should achieve to reduce risk while also offering some resources on how to achieve the outcomes. However, it’s important to understand that the NIST CSF is outcome-focused, not activity-focused. In other words, the NIST CSF describes what organizations should achieve, not precisely how to achieve it. The framework is intentionally designed to be as flexible and widely adoptable as possible.
The NIST CSF describes the outcomes (i.e., the “what” organizations should achieve) across a three-tier taxonomy:
- Functions – high-level cybersecurity outcomes
- Categories – mid-level cybersecurity outcomes
- Subcategories – low-level cybersecurity outcomes
The NIST CSF also offers two resources to help organizations understand how to achieve the outcomes:
- Informative References – mappings between each NIST CSF Subcategory and the cybersecurity controls in other popular frameworks, such as NIST 800-53
- Implementation Examples—a brand new addition to the Core in NIST CSF 2.0. The Implementation Examples describe sample and practical things organizations could do to achieve the intended outcomes of each subcategory. While NIST is quick to point out that the Implementation Examples are not prescriptive, they do serve as a powerful new resource for helping organizations understand the “how.”
2. Organizational Profile
A lesser-known part of the NIST CSF is the Organizational Profile, which is NIST’s language for the process organizations can follow to identify their current cybersecurity outcomes compared to the NIST CSF’s intended outcomes. Organizations can create their own Organizational Profile to illuminate their strengths and gaps. At Sedara, we call this process a Gap Assessment and conduct it all the time for organizations.
3. Implementation Tiers
The NIST CSF also offers a four-tier scoring system organizations can use to self-assess their effectiveness at achieving the intended outcome of a Subcategory:
- Tier 1 – Partial
- Tier 2 – Risk Informed
- Tier 3 – Repeatable
- Tier 4 – Adaptive
Overall, the NIST CSF 2.0 does not substantially change the Organizational Profile and Implementation Tier parts of the framework but makes many changes across the Core.
Core Changes You Should Know
Compared to the previous version of the NIST CSF, the 2.0’s Core has many additions, removals, rewords, and reorganizations. The greatest changes include the addition of the new Govern Function, an increase in the number of Subcategories focused on supply chain management and risk management, and the introduction of Implementation Examples.
1. Function Changes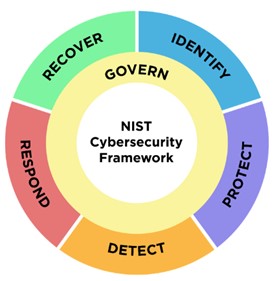
NIST added a brand-new Govern Function to the CSF 2.0, bringing the total number of Functions from five to six. The CSF’s new logo displays the Govern Function in a circle surrounded by the other Functions, emphasizing the importance of governance across all other cybersecurity outcomes.
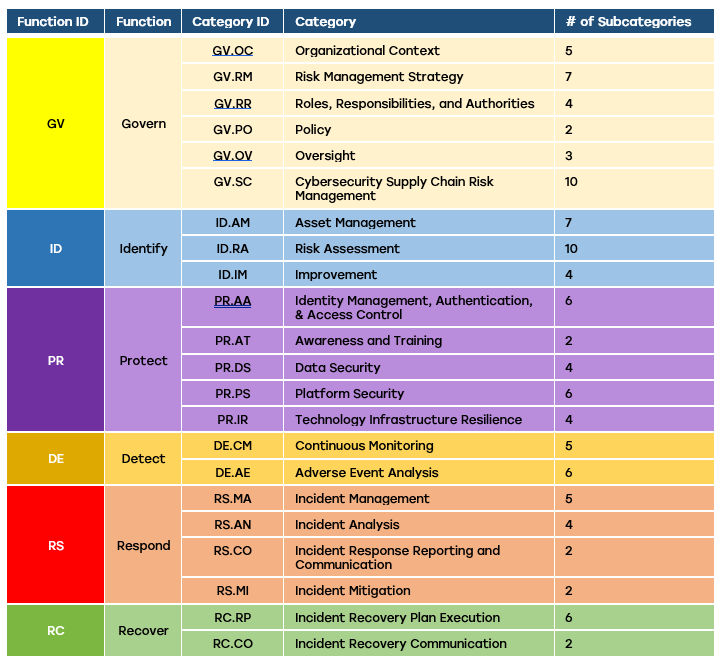
2. Category Changes
Overall, the CSF 2.0 has one less category than the previous version. The original five functions all have at least one less category assigned to them, while the new Govern Function now has the most categories assigned to it.
| Function | CSF 1.1 # of Categories | CSF 2.0 # of Categories |
| Govern | — | 6 |
| Identify | 6 | 3 |
| Protect | 6 | 5 |
| Detect | 3 | 2 |
| Respond | 5 | 4 |
| Recover | 3 | 2 |
| Total | 23 | 22 |
Many categories have been changed, but there are too many to describe here. However, as a few examples, many of the Identify Function’s Categories were moved into the new Govern Function. Many of the Protect Function’s Categories were reworded and redesigned. Lastly, all the Respond and Recover Functions’ Categories now begin with “Incident” to emphasize their relation to incident response management.
3. Subcategory Changes
The NIST CSF 2.0 has 106 Subcategories, two less than the previous version. While there are too many Subcategory changes to describe here, there are some high-level takeaways. For example, the CSF 2.0 doubles the number of supply chain-related Subcategories from five to ten. There are also far more Subcategories focused on organizational leadership and risk management this time. Lastly, two Subcategories now reference “metadata,” and several Response and Recover Subcategories now emphasize the importance of preserving data integrity and backups during an incident.
NIST offers documentation describing how NIST CSF 2.0 Subcategories map to the previous version of the NIST CSF. The documentation lists sixteen NIST CSF 2.0 Subcategories as “conceptually new”, meaning they have no mapping to the previous version of the NIST CSF. Although NIST says these subcategories are conceptually new, long-time users of the NIST CSF or relatively mature cybersecurity programs should not be surprised by them, and they are likely already working towards achieving their intent.
4. Emphasis on Organizational Leadership and Risk Management
One of the biggest changes in the NIST CSF 2.0 is the greater emphasis placed on organizational leaders taking ownership of cybersecurity outcomes and ensuring risk management processes are in place. The introduction of the Govern Function makes this focus clear. Additionally, nearly 1/3rd of all NIST CSF 2.0 Subcategories contain the word “risk” in them, compared to just 1/5th in the previous version. IT and cybersecurity leaders should ensure their executive-level colleagues help define and achieve the organization’s cybersecurity- and risk-related objectives.
5. Greater Logical Consistency of Outcomes
The NIST CFS is logically organized according to Functions, Categories, and Subcategories; however, the previous version of the NIST CSF was sometimes prone to having the same kind of Subcategory outcome described across multiple Functions and Categories. NIST CSF 2.0 reduces this redundancy by improving the logical consistency of the Subcategories. For example, to paraphrase a few Categories and Subcategories, the following trends can be observed:
- Category – Asset Management (ID.AM)
- AM-01: maintain hardware inventories
- AM-02: maintain software inventories
- AM-03: maintain data flow, port, protocol, and service inventories
- AM.04: maintain third party service provider inventories
- AM-07: maintain data type inventories
- Category – Data Security (PR.DS)
- DS-01: protect data-at-rest
- DS-02: protect data-in-transit
- DS-10: protect data-in-use
- Category – Continuous Monitoring (DE.CM)
- CM-01: monitor networks
- CM-02: monitor physical environment
- CM-03: monitor personnel activity
- CM-06: monitor third-party service provider activity
- CM-09: monitor computing activity
6. Leverage the Implementation Examples
The Implementation Examples are among the most significant enhancements to the NIST CSF 2.0. Be sure to review them when working with the NIST CSF, as they can help define the intent of the Subcategory and generate new people, processes, or technology controls to add to your cybersecurity program.
Conclusion
Overall, the NIST CSF 2.0 enhances the capabilities of the NIST CSF to serve as a holistic cybersecurity framework for organizations of any size in any sector. The new version of the framework does not include anything drastically new—like AI security controls—but it does enhance the utility of its Core and adds new features with the Implementation Examples. Organizations seeking to begin or mature their cybersecurity programs should adopt a cybersecurity framework to guide their activities, and the NIST CSF is one of the best frameworks for this purpose. With the greater emphasis placed on governance and risk management in the NIST CSF 2.0, organizational leadership, not just IT, should help define and accomplish cybersecurity objectives.
We Can Help
Sedara’s Cybersecurity Development Program (CDP) and its trained virtual Chief Information Security Officers (vCISOs) can help you build a successful cybersecurity program that reduces risk. Our vCISOs serve as your expert, trusted advisors on all things cyber and are skilled in all the major cybersecurity frameworks. We can help you adopt the NIST CSF and build, mature, and sustain your own cybersecurity program.
More Reading on This Topic
- NIST CSF website: https://www.nist.gov/cyberframework